De.Fi REKT Report: A Quarter in Review - Almost 415 Million Lost in Q1 2024
During Q1 2024 ... total losses amounting to $414,875,820 across a range of exploits and security incidents.
- Key Points
- Observable Trends in DeFi Exploits
- Funds Recovered
- Types of Exploits in Q1
- Attack Vectors
- Top Five Losses in Q1
- Cщnclusion
- About De.Fi
- Free Security Bible (Book)
De.Fi maintains and updates the largest database of hacks, scams and exploits in crypto via the Rekt Database
While all attention has been on the unfolding banking crisis and a subsequent uptick in the Bitcoin market, we saw crypto losses mount to a 9-figure amount in March, and for the second month in a row. Hackers and scammers are upping the stakes as we count a total loss of close to $400 million in the first quarter of the year.
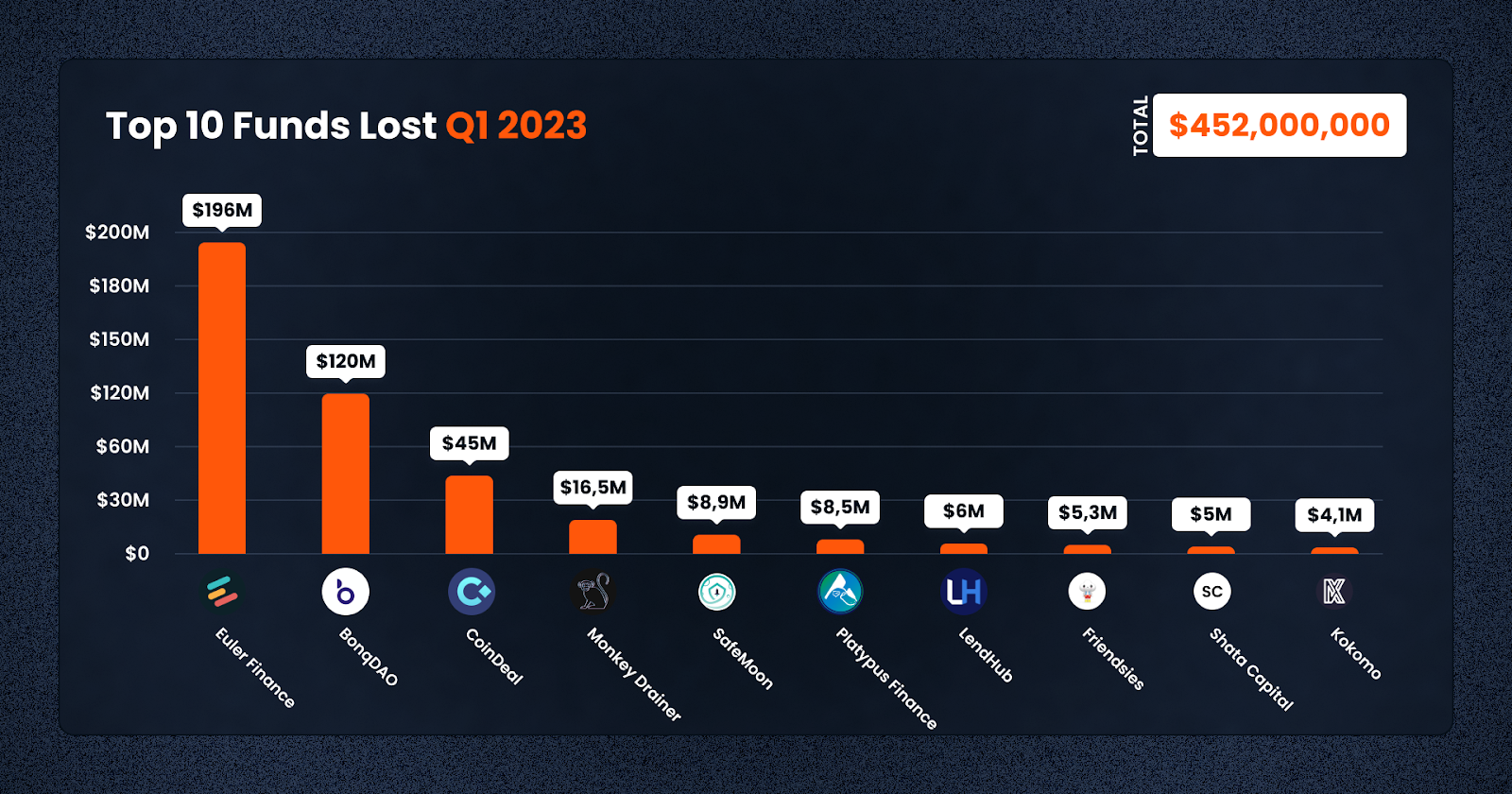
Out of the $452m lost in Q1, a total of $215m was lost in just the first 20 days of March, underscoring the rapid pace at which scammers have been operating in recent weeks.
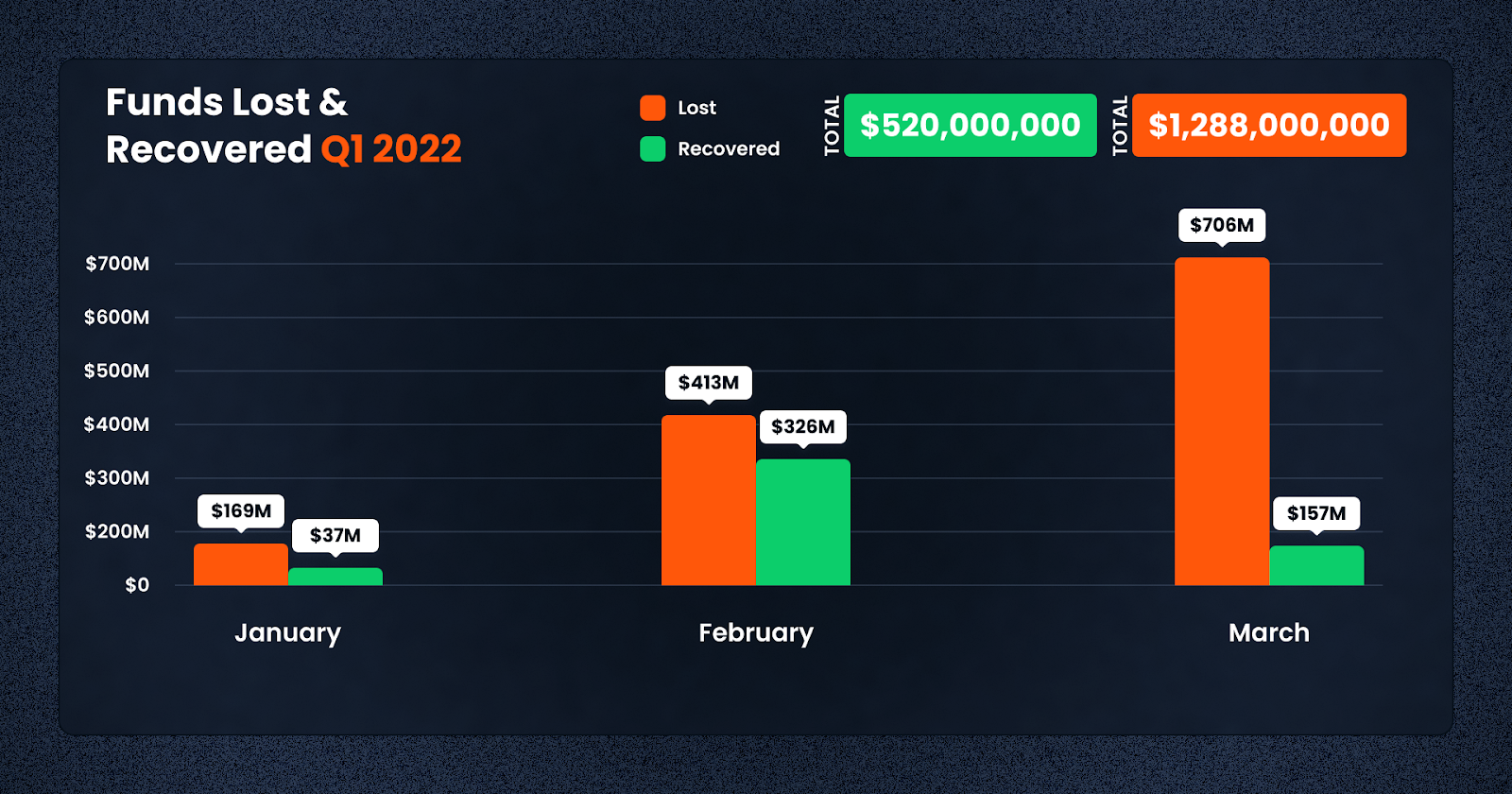
While these losses are staggering, they also mark a decrease as compared to the same period in 2022, wherein Q1 saw $1.3 billion lost. Here’s a comparison:
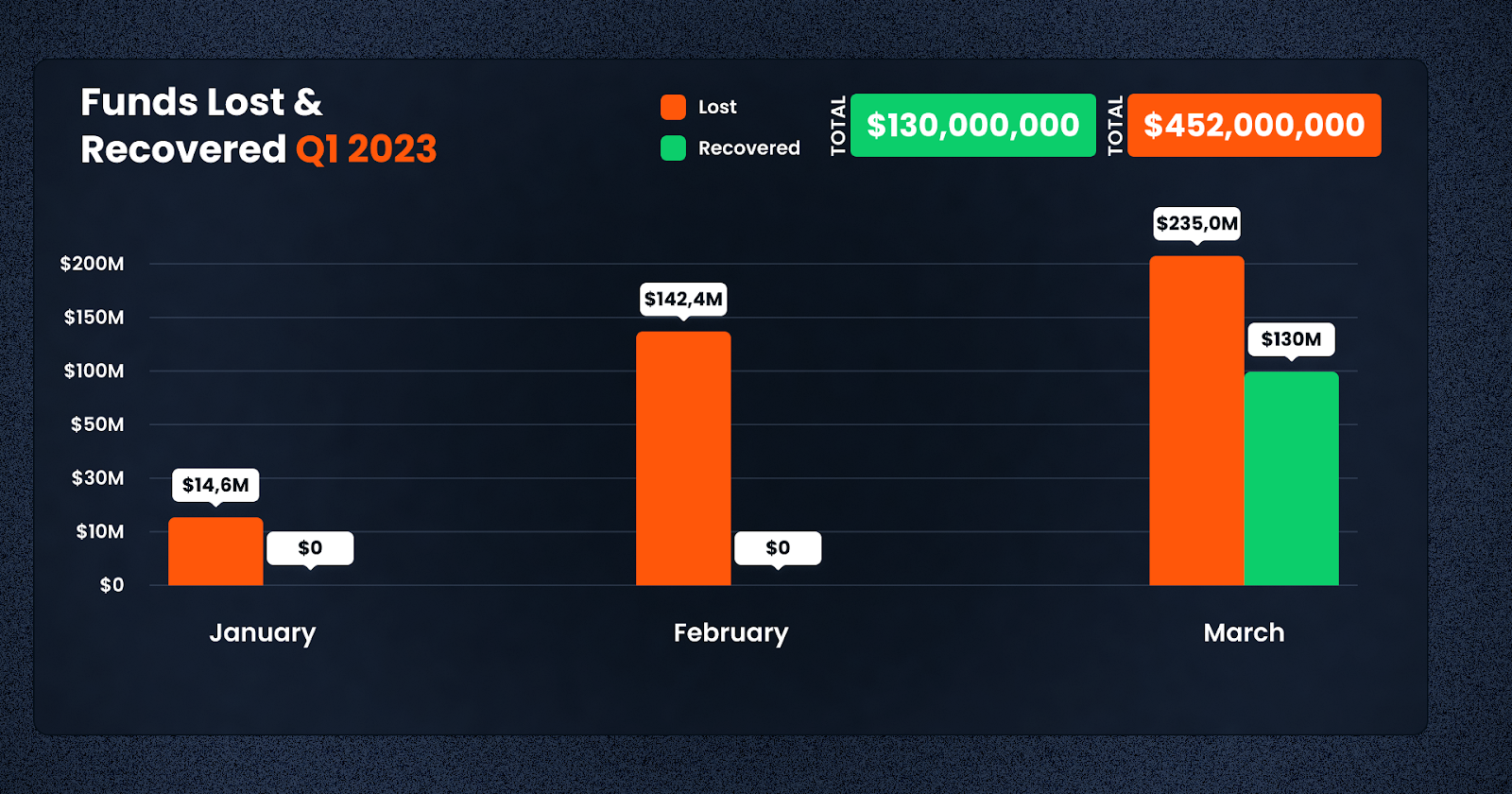
In total, $130m was recovered in Q1 this year, marking a recovery rate of 28.7%. This figure was $520m in 2022, meaning that 40% of funds were recovered in the same month last year.
Let’s take a brief look at the top cases this quarter. We will then explore more in details the top 5 cases in Q1.

As can be seen from the scale of the losses in Q1, a large majority of losses came from two protocols, Euler and BonqDAO — which together amounted to over $316 million being lost.
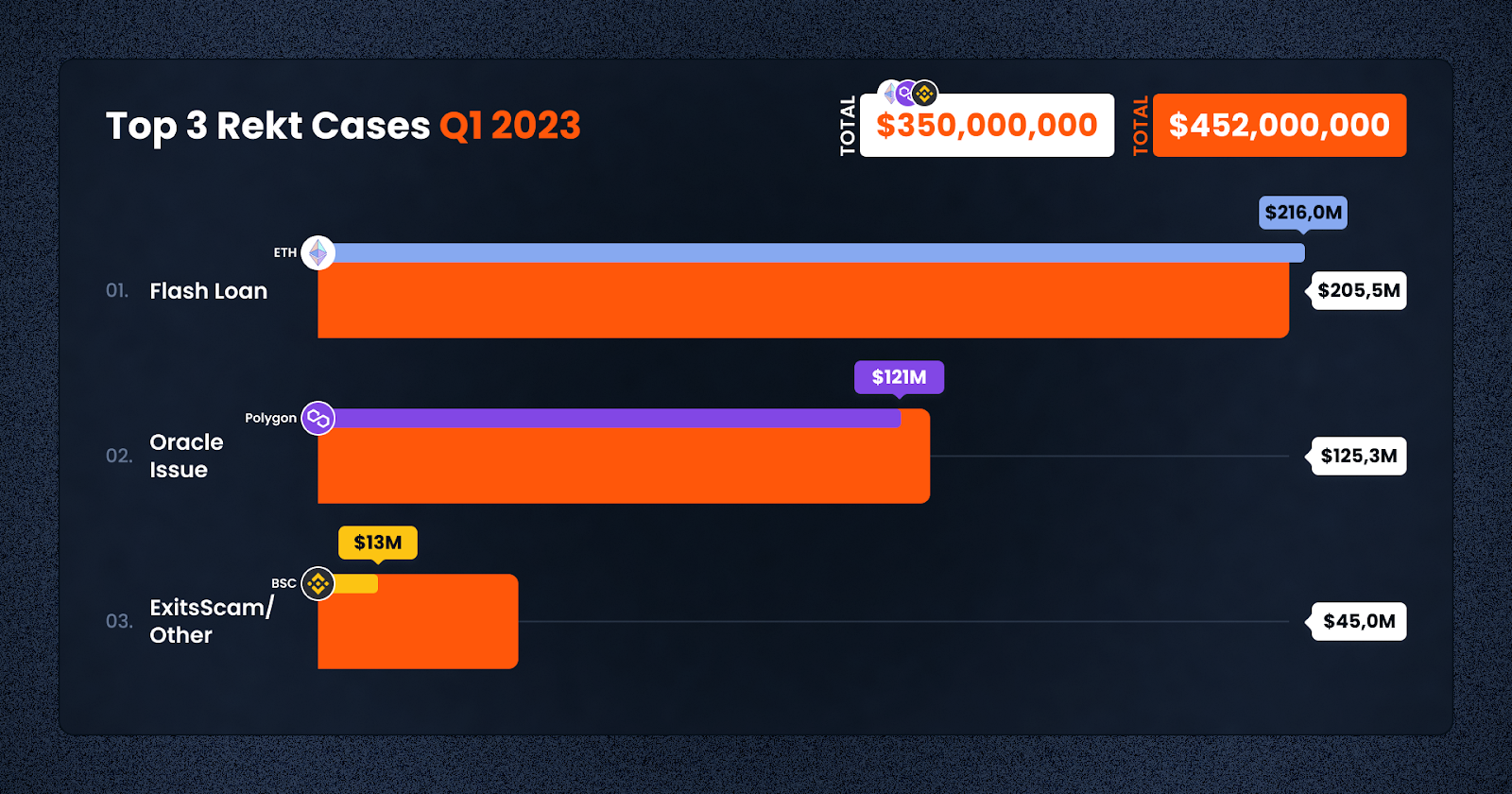
Notably, this means that the biggest losses this quarter were due to Flash Loan issues, which have been becoming increasingly common in recent months: Over $200m was lost through this channel.
This also makes Ethereum the chain where the highest losses were recorded in these first three months of the year.
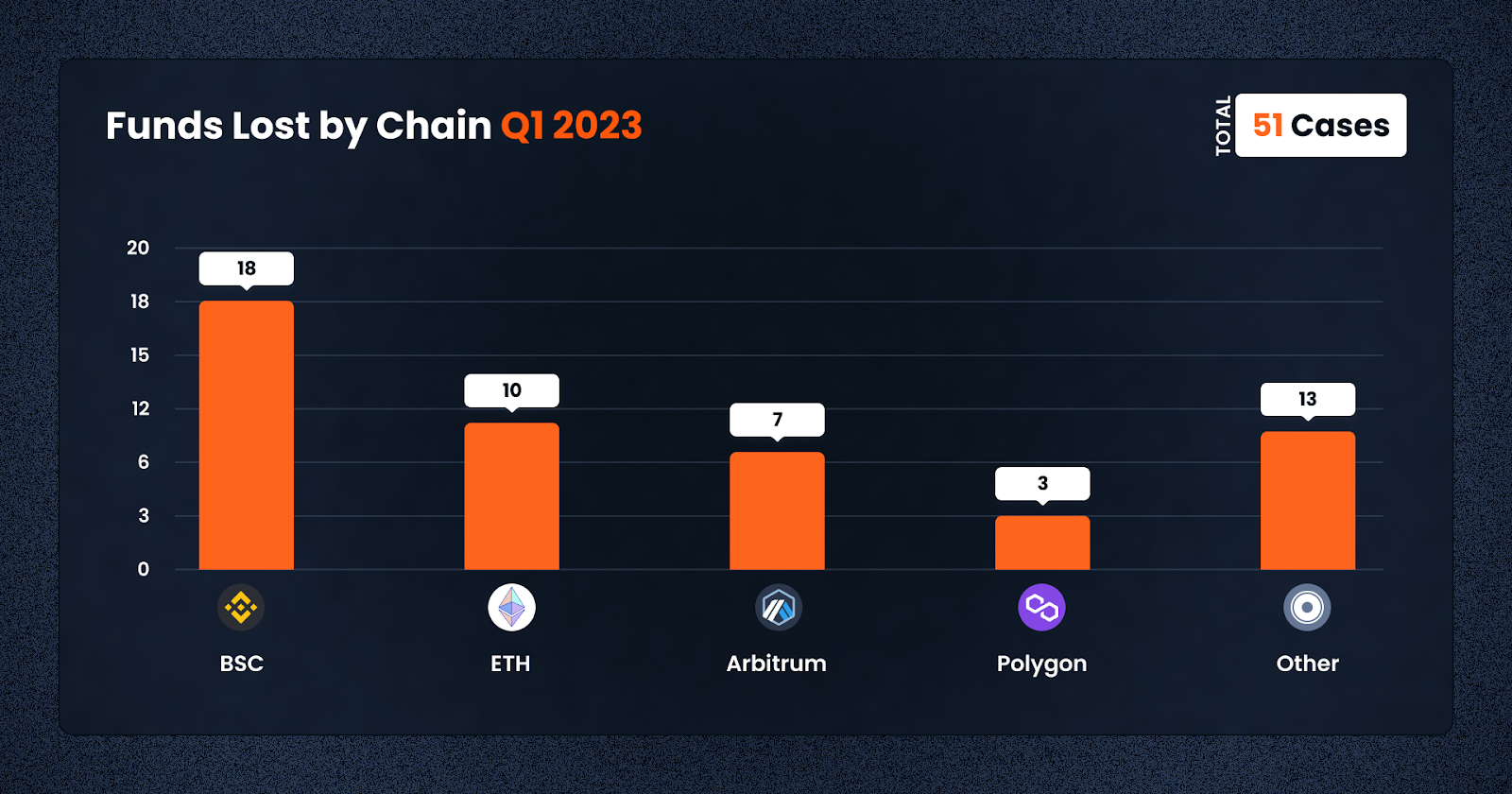
Meanwhile, BNB Smart Chain unfortunately remains popular for crypto criminals, with a whopping 18 cases happening in the first three months of the year, almost double that of its closest peers, with 10 on ETH and 7 on Arbitrum.
In Q1, $130m was ultimately recovered. The whole amount was recovered in March, leaving January and February the rare months when 0$ was recovered in crypto hacks & scams.
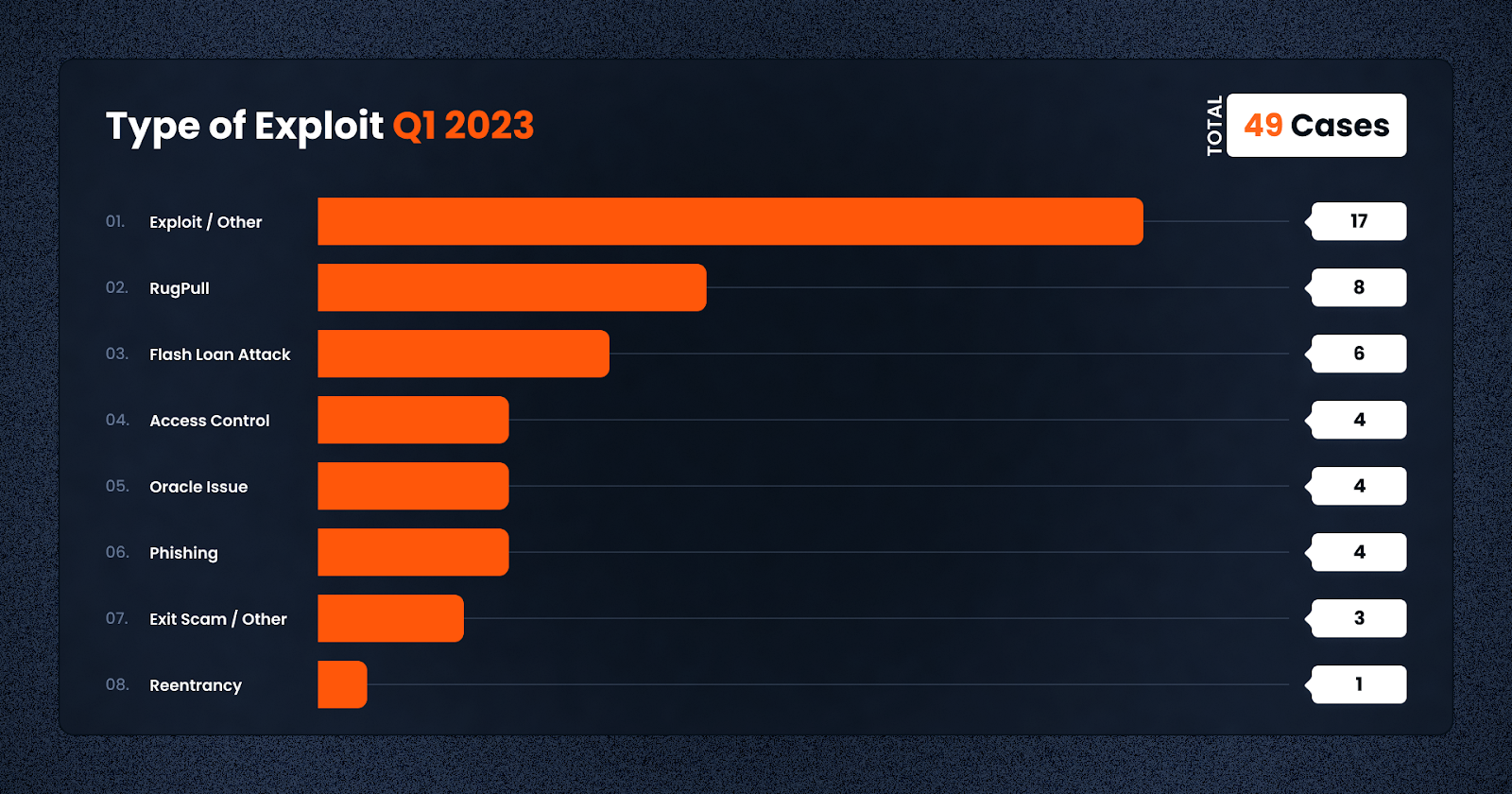
In terms of frequency, smart contract exploits were the most popular among criminals at a total of 17 instances. This was followed by the rug pull and flashloan attack, at 8 and 6 cases respectively — the latter which resulted in a majority of the losses in March.
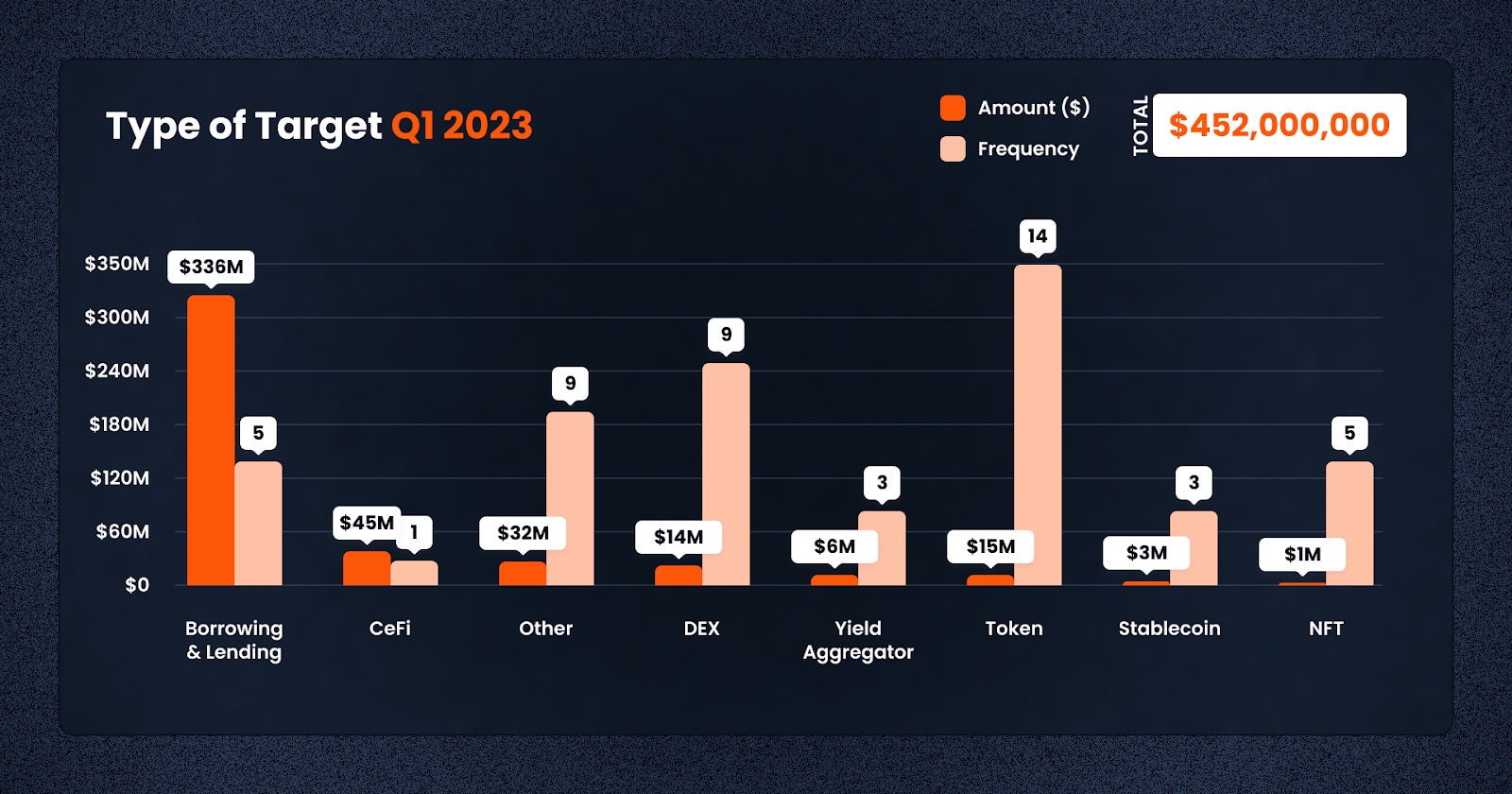
In terms of attack vectors, Tokens proved to be the most popular targets this year so far — this is unsurprising given that tokens are easy to deploy, and prey on the fear of missing out experienced by many new crypto investors. This is especially true with the market comeback in recent days. In terms of amounts lost, though, Lending and Borrowing protocols took the prize, though this was driven by a small number of high profile events — Euler Finance and BonqDAO.
On March 13th, Euler Finance, a prominent Ethereum-based noncustodial lending protocol, fell victim to a devastating flash loan attack. The breach led to the loss of millions of dollars worth of various cryptocurrencies, including Dai, USD Coin (USDC), staked Ether (StETH), and Wrapped Bitcoin (WBTC). The attacker executed multiple transactions, making away with a staggering total of nearly $196 million.
Detailed on-chain data revealed the theft included $8.7 million in Dai, $18.5 million in Wrapped Bitcoin, $135.8 million in Staked Ethereum, and $33.8 million in Circle’s USD stablecoin, USDC. Meta Sleuth, a reputable crypto analytic firm, drew parallels between this attack and a deflation attack that occurred only a month prior.
The attacker utilized a multichain bridge to facilitate the transfer of funds from the Binance Smart Chain (BNB) to the Ethereum network. Upon successfully moving the funds, the attacker commenced the flash loan attack. To further cover their tracks, the stolen funds were deposited into Tornado Cash, a well-known crypto mixer, complicating recovery efforts.
On March 25th, over 51,000 ether, valued at nearly $90 million as of Saturday, was sent back to the Euler deployer contract in early U.S. hours.
On March 27th, the hacker returned the additional $39M in 3 transactions.
Block Data Reference
Funds Return Tx:
Examples of exploit TXs:
Attacker addresses:
Attacker contracts:
On 2 February, BonqDAO and AllianceBlock, two blockchain-based platforms, suffered a major loss of $120 million due to a vulnerability in the BonqDAO smart contract. The exploit has forced the suspension of trading and liquidity to prevent the stolen tokens from being converted into other assets. The Bonq protocol has also since been suspended, and the team is currently working on a solution to enable users to withdraw the remaining collateral.
The BonqDAO exploit occurred when its price oracle was manipulated, resulting in an increase in the WALBT price. This allowed the attacker to mint over 100 million BEUR. The attacker then manipulated the WALBT price and liquidated multiple troves, enabling them to withdraw 113.8 million WALBT and 98 million BEUR, with a combined value of over $10 million.
The dumping of these illicit gains resulted in a significant drop in the value of both WALBT and BEUR. The WALBT price dropped by more than 50%, and the BEUR price dropped by 34%. As a result, the total loss for BonqDAO and AllianceBlock was estimated to be $120 million.
Block Data Reference
Examples of exploit TXs:
Exploiter address:
The U.S. Securities and Exchange Commission (SEC) has recently filed charges against a group of individuals and companies implicated in the CoinDeal investment scheme. This fraudulent operation reportedly raised over $45 million through the sale of unregistered securities, ultimately defrauding tens of thousands of unsuspecting retail investors.
The individuals charged in the scheme include Neil Chandran, Garry Davidson, Michael Glaspie, Amy Mossel, and Linda Knott, along with two unnamed companies. The SEC alleges that the defendants falsely promoted CoinDeal, a purported blockchain technology company, as having been sold for trillions of dollars. They claimed that investors would generate substantial returns by investing in the venture.
However, the SEC’s investigation revealed that the defendants misappropriated millions of dollars from investor funds for their personal use. Among other luxury items, Chandran allegedly used the stolen funds to acquire cars, real estate, and a boat. The SEC is now seeking to recover the misappropriated funds, along with pre-judgment interest and penalties. They are also pursuing permanent injunctions against all the defendants.
Neil Chandran is currently behind bars, awaiting trial in a separate investment fraud case overseen by the U.S. Justice Department. As regulators work to dismantle the CoinDeal scheme, the case serves as a stark reminder of the need for vigilance in the rapidly evolving world of digital assets and blockchain technology.
The Monkey Drainer phishing group announced in March on their Telegram channel that they are shutting down their illicit service. The group, which specialized in providing phishing smart contracts, reportedly stole a staggering $16,506,602 before ceasing operations.
Monkey Drainer’s tactics involved supplying malicious smart contracts with unverified source code to unsuspecting users. These contracts were designed to drain the wallets of affected individuals, stealing native coins, ERC20 tokens, and NFTs across various blockchain networks, including Ethereum, Binance, and Avalanche. The group took a 30% cut of the stolen funds as payment for their services.
Following the announcement, the Monkey Drainer hacker claimed that all files related to the operation had been immediately deleted. SlowMist, a blockchain security firm, confirmed the total stolen amount reached $16,506,602. The sudden closure of the group highlights the ongoing threats posed by phishing scams in the cryptocurrency space and the need for increased vigilance among users and platforms alike.
Block Data Reference
Malicious contract example:
Platypus Finance, an automated market maker (AMM) offering stableswap opportunities, recently fell victim to a flash loan attack. The perpetrator exploited several asset contracts within the protocol using an unverified malicious smart contract, ultimately stealing $8,500,887 in stablecoins. The stolen assets included around 4,400,000 USDC, 2,700,000 USDT, 687,000 BUSD, and 691,000 DAI.
The attacker took advantage of a vulnerability in the USP solvency check mechanism, securing a flash loan of 44,000,000 USDC. They then swapped the loan for 44,000,000 Platypus LP-USD and minted 41,700,000 USP tokens at no cost. These tokens were subsequently exchanged for various stablecoins. At the time of reporting, the Platypus Finance team was collaborating with third-party services like Binance, Tether, and Circle to freeze the stolen assets, and USDT has already been successfully frozen.
Despite these efforts, the attacker managed to transfer 2,403,165 USDC through the Gnosis Proxy, moving a portion of the stolen funds. In response, the Platypus Finance team identified and removed the malicious contract and has since implemented additional security measures to prevent similar attacks in the future.
Block Data Reference
Malicious transaction:
Attacker’s address:
Malicious contract:
Transfer transactions:
In conclusion, the significant surge in financial losses this quarter underscores the need for heightened risk management and vigilance when investing in the decentralized finance (DeFi) sector. It is crucial for investors to educate themselves on potential dangers and implement appropriate measures to protect their investments. At De.Fi, we acknowledge the importance of offering guidance in navigating the intricate and constantly evolving DeFi environment. As such, we are committed to equipping our users with the necessary resources to make well-informed investment choices within the industry.
De.Fi is an all-in-one Web3 Super App and Antivirus featuring an Asset Management Dashboard, Opportunity Explorer, and the world’s first Crypto Antivirus powered by the largest compilation of DeFi hacks and exploits, the Rekt Database. Trusted by 600K users globally, De.Fi aims to drive DeFi adoption by making the self-custody transition as simple and secure as possible. Backed by Okx, Huobi, former Coinbase M&A, and used by large companies worldwide, including University College London and Coingecko.
*Website | Twitter | De.Fi Security | Rekt Database*
Right now we are GIVING AWAY free copies of Security Bibles — the most comprehensive DeFi Security Guide brought to you by the De.Fi Team!
During Q1 2024 ... total losses amounting to $414,875,820 across a range of exploits and security incidents.
Among the many options available, Phantom Wallet has emerged as a popular choice for those in the Solana ecosystem, sparking questions about its safety, legitimacy, and features.
A total of $148,690,165 was lost across various platforms and chains due to diverse exploits.
Celo token approvals can go by many names including token permissions, smart contract permissions, token allowances, etc.
The top three largest governance hacks resulted in $414M in losses over the years
MetaMask is one of the most commonly used DeFi wallets, and users most often encounter token approvals in the wallet via the “MetaMask custom spending cap" prompt.
© De.Fi. All rights reserved.